The Internet Assigned Numbers Authority (IANA) is the body that manages the unicast IPv4 address pool (ie from 0.0.0.0 to 223.255.255.255.255). IANA assigns blocks of this space to the 5 RIR's (Regional Internet Registries) i.e. AFRINIC, APNIC, ARIN, RIPENCC and LACNIC. The RIR's use their distribution policies to further allocate addresses to local registries and ISP's which propogate them to the endhosts.
Potaroo.net predicts the following dates for the exhaustion of IPv4 address space.
Projected IANA Unallocated Address Pool Exhaustion: 04-Feb-2011
Projected RIR Unallocated Address Pool Exhaustion: 05-Mar-2012
A live down-counter counting number of days until we hit exhaustion of the IPv4 address space can be found
here . This counter is generated using data from potaroo.net report The report is pretty detailed and explains the modelling used for predicting the dates. Please note that the modelling is based on current address distribution policies used by RIRs and current consumption trends. The following graph (from potaroo.net report) shows the current status of IPV4.
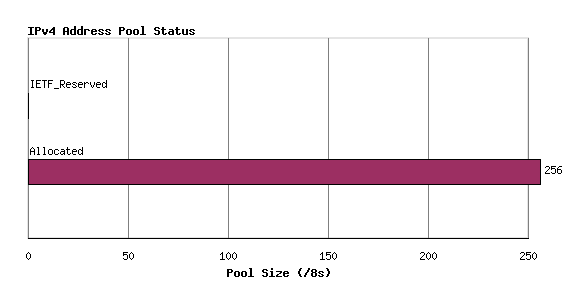
An explanation of the graph follows:
Note that there are 256 /8's where each /8 is 16,777,216 addresses.
IETF_Reserved : Blocks reserved for special purpose. It consists of 16 /8 Multicast blocks + 16 /8 reserved blocks + 1 /8 (0.0.0.0/8) block for local identification + 1 /8 (127.0.0.0/8) for loopback + 1 /8 (10.0.0.0/8) for personal use + 1 /8 (14.0.0.0/8) for public-data networks.
IANA_Pool : Pools of /8 left with IANA for allocation to RIRs.
Allocated : Allocated by IANA to RIR. This does not reflect current consumption because RIRs may have a pool of their own.
So much for IPv4. Now lets look at IPv6.
In 2008, there have been atleast 2 big studies around the state of IPv6.
The reports are detailed but these are a few interesting points.
1) Arbor networks experiment measured the total amount of IPv6 flowing in the backbone , and they note that
At its peak, IPv6 represented less than one hundredth of 1% of Internet traffic.
2) The biggest reason cited in the summary for the above observation is money.
Specifically, the department of commerce estimates it will cost $25 billion for ISPs to upgrade to native IPv6.
3) Googles effort measures the state of IPv6 from a end node perspective as opposed to the Arbor measurement. Their key observations are :
- 0.238% of users have useful IPv6 connectivity (and prefer IPv6).
- 0.09% of users have broken IPv6 connectivity.
- Probably a million distinct IPv6 hosts exist.
- Russia leads the chart in IPv6 penetration.
- IPv6 prevalance is low but increasing steadily by the week.
- IPv6 - IPv4 tunelling is the most common transition mechanism.
- MacOS has better IPv6 penetration than Vista because of its default policies in the OSes.
So given the predictions about end of IPv4 and the rate of adoption of IPv6, are we ready for migration? In Feb 2008, ICANN added IPv6 addresses for 6 of the 13 root DNS servers (news here) which is a step in the right direction but is it enough to prod people to migrate?
I have the following concerns about the migration:
- What would dictate the migration: economics or a better-future-internet?
- Will ISPs be willing to pay the price?
- Even if they are willing to do so, can the consumers and business transition to IPv6 seamlessly?
- Will security products continue working the same way?
- Are the vendors testing their implementations with IPv6 to make a simple software update to the tons of software already out there?
- How will this migration be different in impact than the Y2k bug of the last century? Are these comparable in any sense?
I have a feeling that economics will dominate this race more than anything else. If the migration is going to cost a lot of money for businesses without any added value then there is bound to be a huge pushback. Somehow the cost has to be justified to them to make this transition happen and just saying address space exhaustion may not strike a chord with every business.